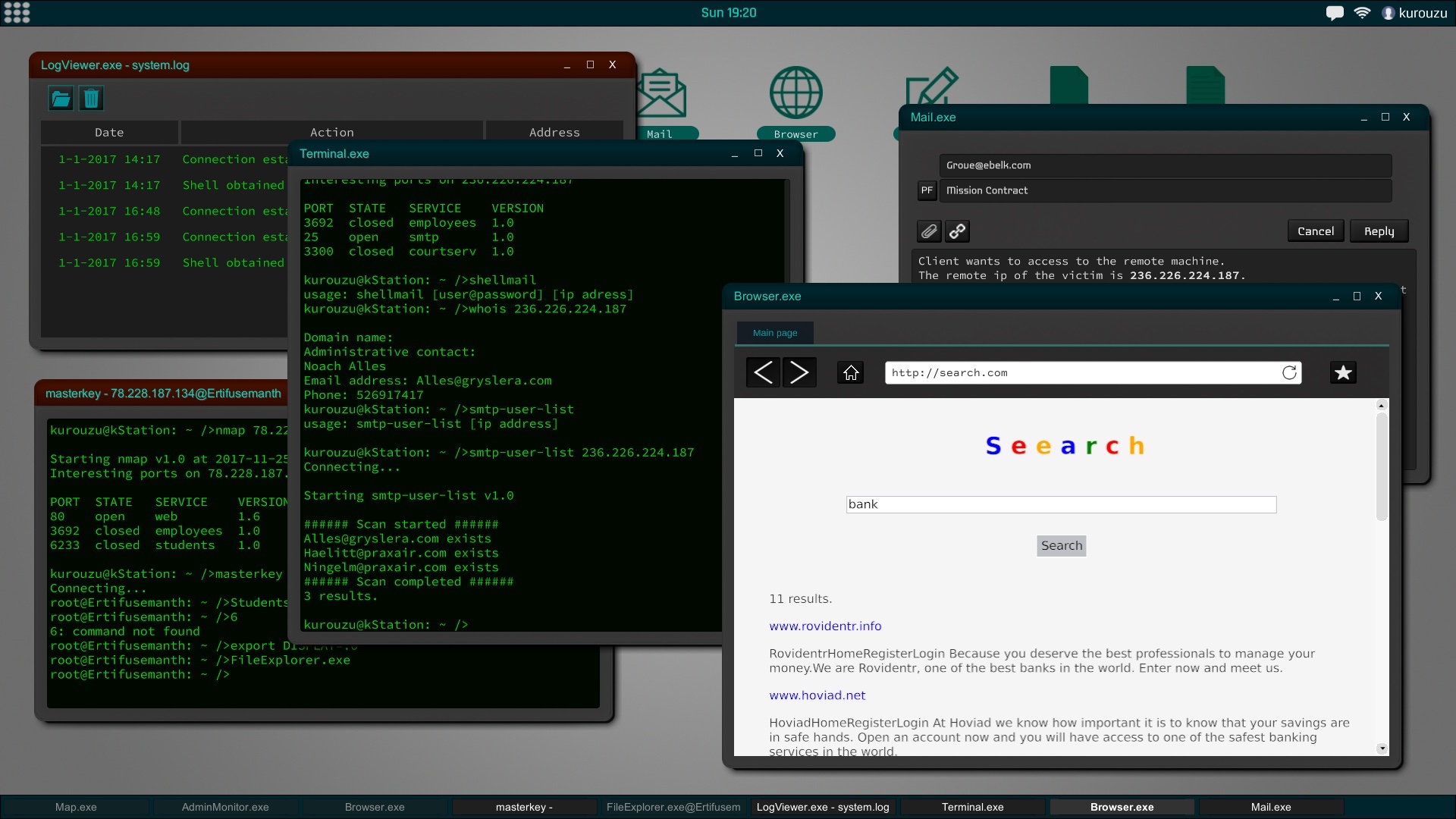
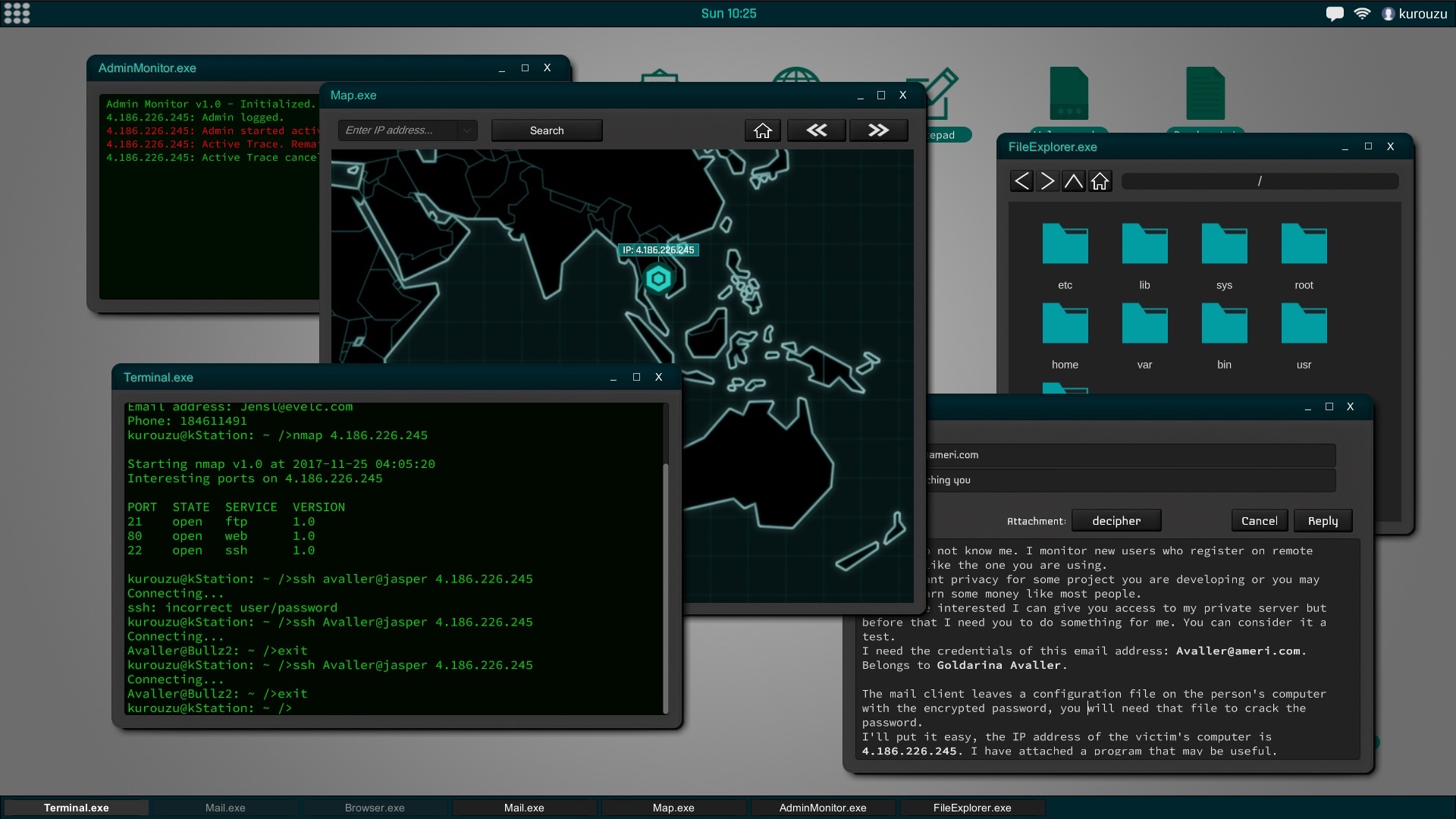
You're a hacker with full freedom to act as you want on a vast network of computers procedurally created. Each player action influence the world and therefore the other players.
Act for your own benefit, even if it causes collateral damage, help authorities to apprehend criminals or simply keep a low profile and take advantage of the actions of other players.
The interface of the game is similar to a current desktop operating system. The file explorer, the command terminal or text editor are some of the programs that will be available from the start of the game. As you improve your skills you will encounter new utilities may install and use.
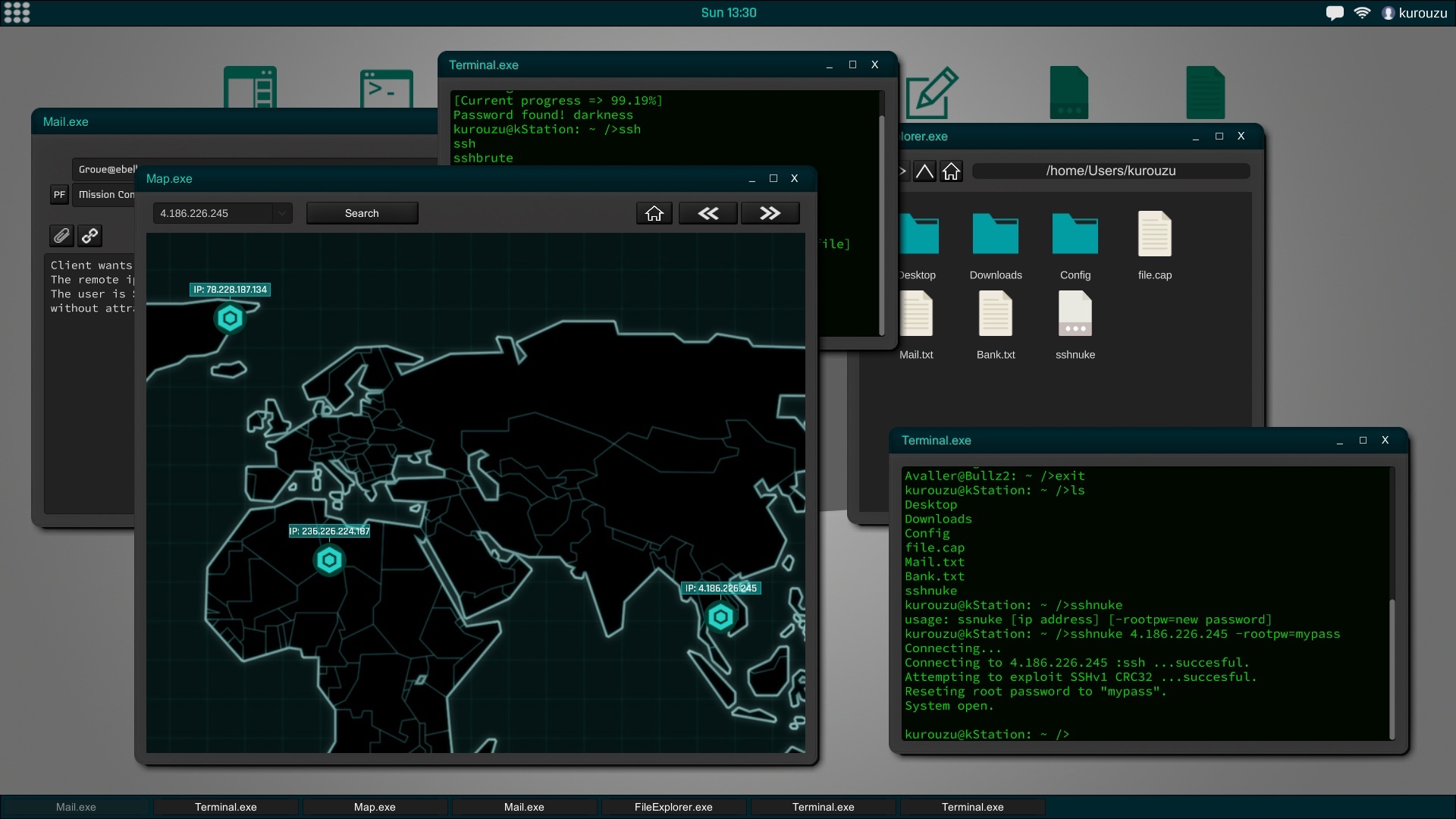
In Grey Hack, terminal has a fundamental role, it is also based on actual unix commands and will be an indispensable tool to perform successfully hacking actions.
General
Explore the network freely to discover its secrets and missions.When you increase your reputation on the network you can choose to join a group of hackers to carry out coordinated attacks or even create your own. Although if you prefer you can choose to go solo.
Keep in mind that a hacker does not have to act economically, so you decide which missions you accept and if you agree with its consequences.
Network
All computers and networks are generated procedurally to create a new experience in each game. According to the type of network the security will vary to the point of making practically impossible the penetration in certain systems according to the experience and ability that you have.Social engineering is a powerful tool and, in the most difficult cases, can be very helpful. This means that you can try to trick the user of that computer into giving you their credentials, confidential information about another person, etc.
Going to improve your work station will also be important for more and more professional jobs.
World
Each computer in the network is used by at least one user. Each user lives consistently in the world; go to work, shop online, etc. You can impact directly or indirectly in the life of these people in function of what you do.Main Features
- Simulator based on real UNIX commands.
- Operative system UI completely customizable.
- Share the same world with hundreds of players.
- Freedom to choose the type of hacker you want to be.
- Network and world generated procedurally.
- Online data persistence, allowing you to continue later in the same world and with the same computer after leaving the game.
The public build has been updated with the latest available version of the game!
Version 0.7 brings important features such as Scripting, a renewed Exploits System, support for macOS, community translations and more interesting things, as well as bugfixes.
Keep in mind that version 0.7 is not yet complete and its development will continue in the next cycle of the Nightly Build, which will be available very soon.
You can check the updated Roadmap here.
Below you have a list of the most important changes and additions:
Scripting System

Now you can program your own tools and exploits.
The game scripting completely changes the internal operation of the programs, since instead of being "hardcoded" in the game, now they will use the same APIs that players can use to create their own programs.
This means that, for example, you can check the nmap source code, modify it and compile it in the game. This mechanics will be applied to all existing programs, as well as to the exploits system.
You can check the source code of these programs from the Manual.
NOTE: Some commands have not yet been migrated to the scripting system. In subsequent updates the remaining commands will be migrated.
If you are not interested in programming, you can continue playing and progressing in the game normally, since these changes are transparent to players who do not wish to program.
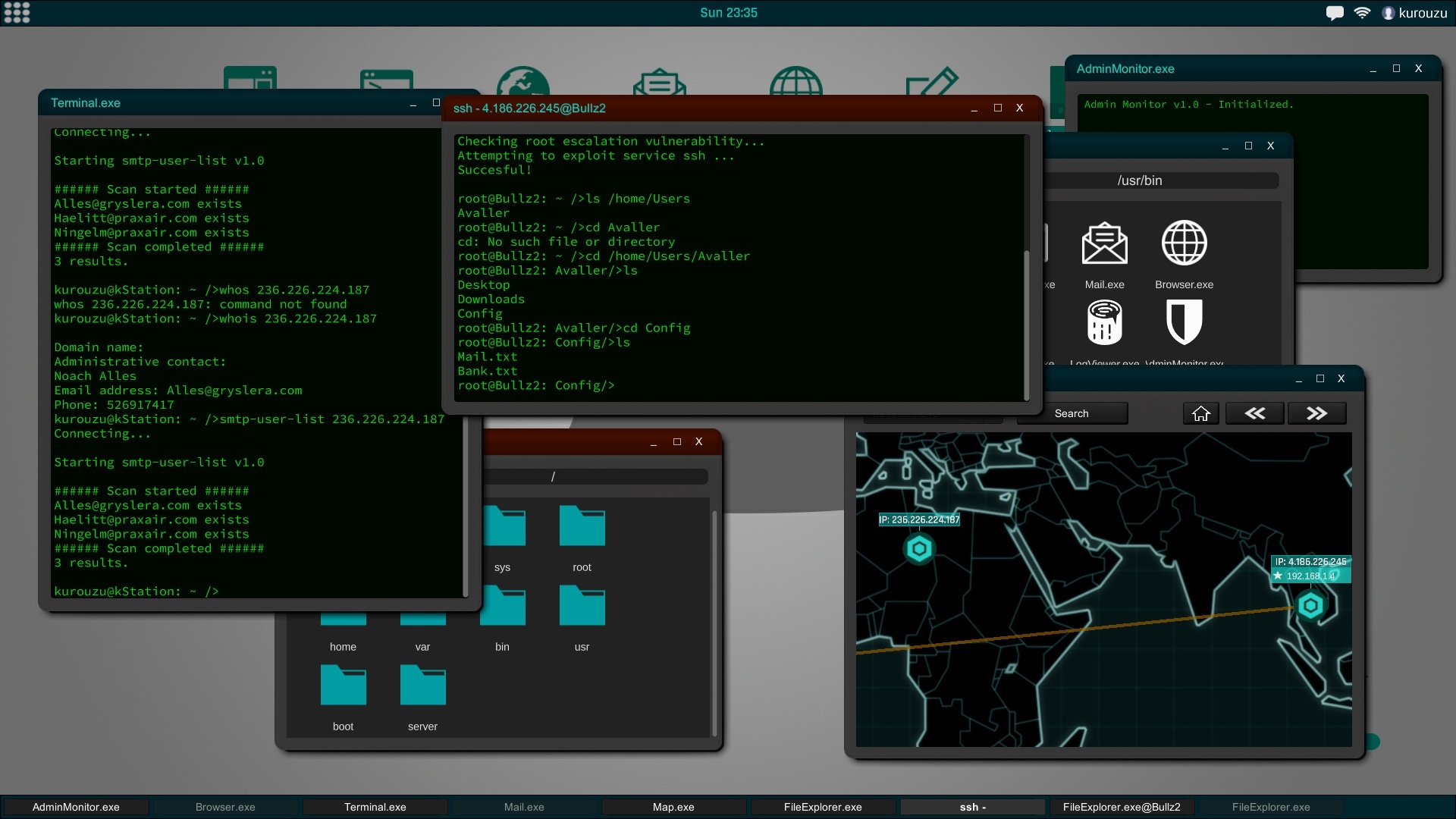
Renewed Exploits System

The Exploits System has been completely renewed, with a deeper and more dynamic system.
This system is based on the libraries stored in the OS. Now some programs need to have certain libraries installed to work. In next updates this number will be increased.
Currently the system has ready the main vulnerability, buffer overflow, on which exploits and attacks that can be made are based. In the next updates this system will expand to add more modules and therefore more actions as well as other main vulnerabilities besides buffer overflow, such as code injection and more.
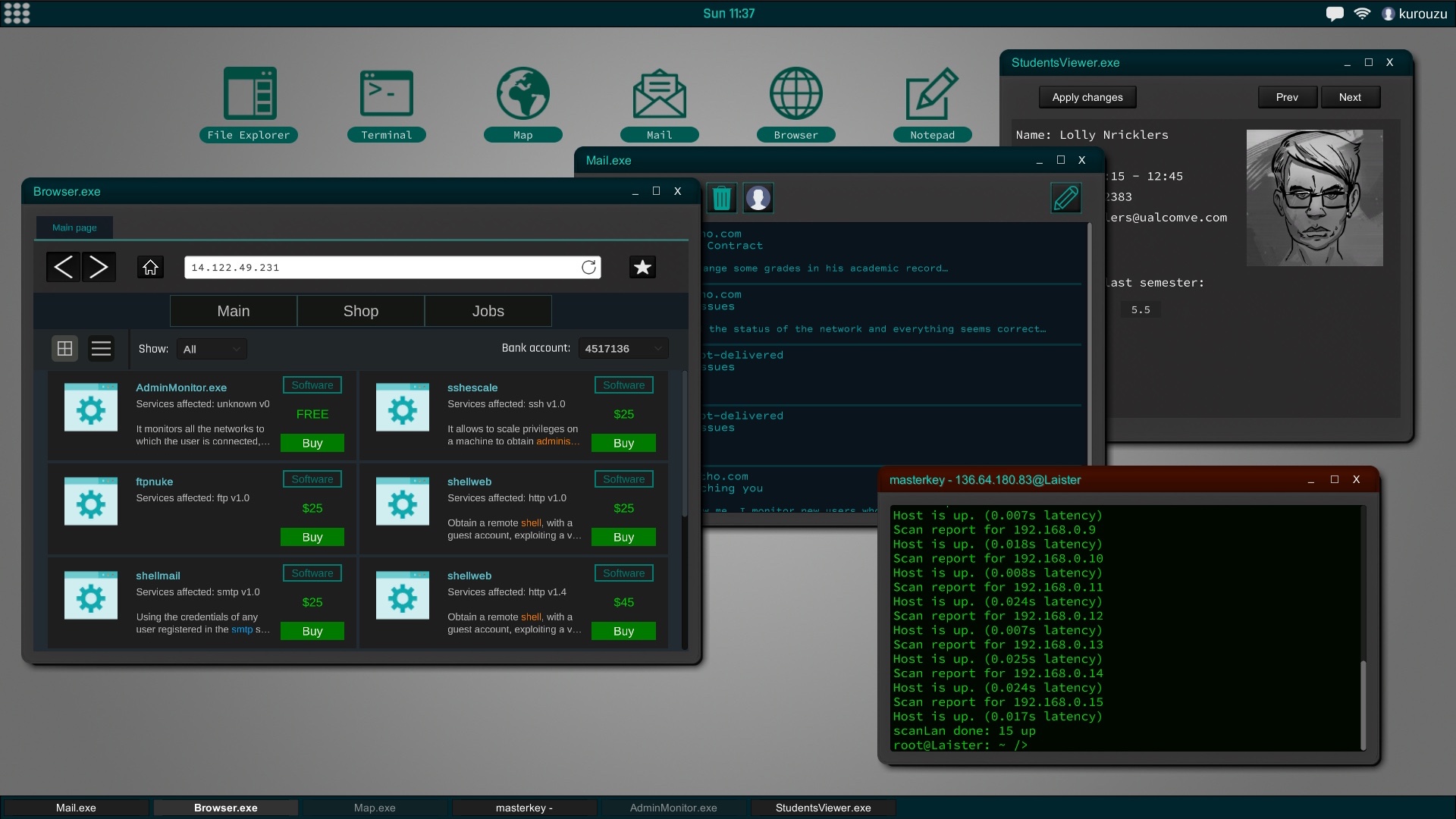
If you prefer not to program, you can buy and download the tools and exploits of the Hackshops, as usual, to perform your jobs.
Improved Trace System

The Trace System is now less aggressive, an admin will not perform a passive trace against a player if he is currently performing one against him, even if it is a different action. This avoids repeated trace catches from the same admin in short periods of time.
Now when the trace system catches a player, he will be notified up to two times of the infraction, the third warning will be the game over.
The Game Over screen and the warning notices show the Administrator information and the network from which the trace was made.
Renewed Game Network System
The network layer used by the game has been completely replaced by a lightweight, secure and more stable solution.With the new network system the game server uses less resources, there is better control of the lag with respect to client connections and therefore the random disconnections that sometimes occurred without apparent pattern should be solved, in addition to other network instabilities.
New commands and tools
New commands based on real UNIX commands have been added, including chown, chgrp, groupadd, groupdel, etc as well new tools available in the Hackshops that will help you to perform your attacks.macOS support
Official support for macOS has been added!The game is compatible with version 10.12 (Sierra) or newer.
Community Translations
An option has been added to create and download community translations through Steam Workshop. If you want to collaborate by adding a translation you can check the guide here:https://steamcommunity.com/sharedfiles/filedetails/?id=1870306717
More news soon!
Minimum Setup
- OS: Ubuntu 18.04. Ubuntu 20.04 and CentOS 7
- Processor: x64 architecture with SSE2 instruction set supportMemory: 512 MB RAM
- Memory: 512 MB RAM
- Graphics: OpenGL 3.2+. Vulkan capable
- Storage: 545 MB available space
[ 6419 ]
[ 5753 ]
[ 1960 ]
[ 2357 ]
[ 713 ]
[ 1040 ]
[ 32768 ]
[ 859 ]