You're a hacker with full freedom to act as you want on a vast network of computers procedurally created. Each player action influence the world and therefore the other players.
Act for your own benefit, even if it causes collateral damage, help authorities to apprehend criminals or simply keep a low profile and take advantage of the actions of other players.
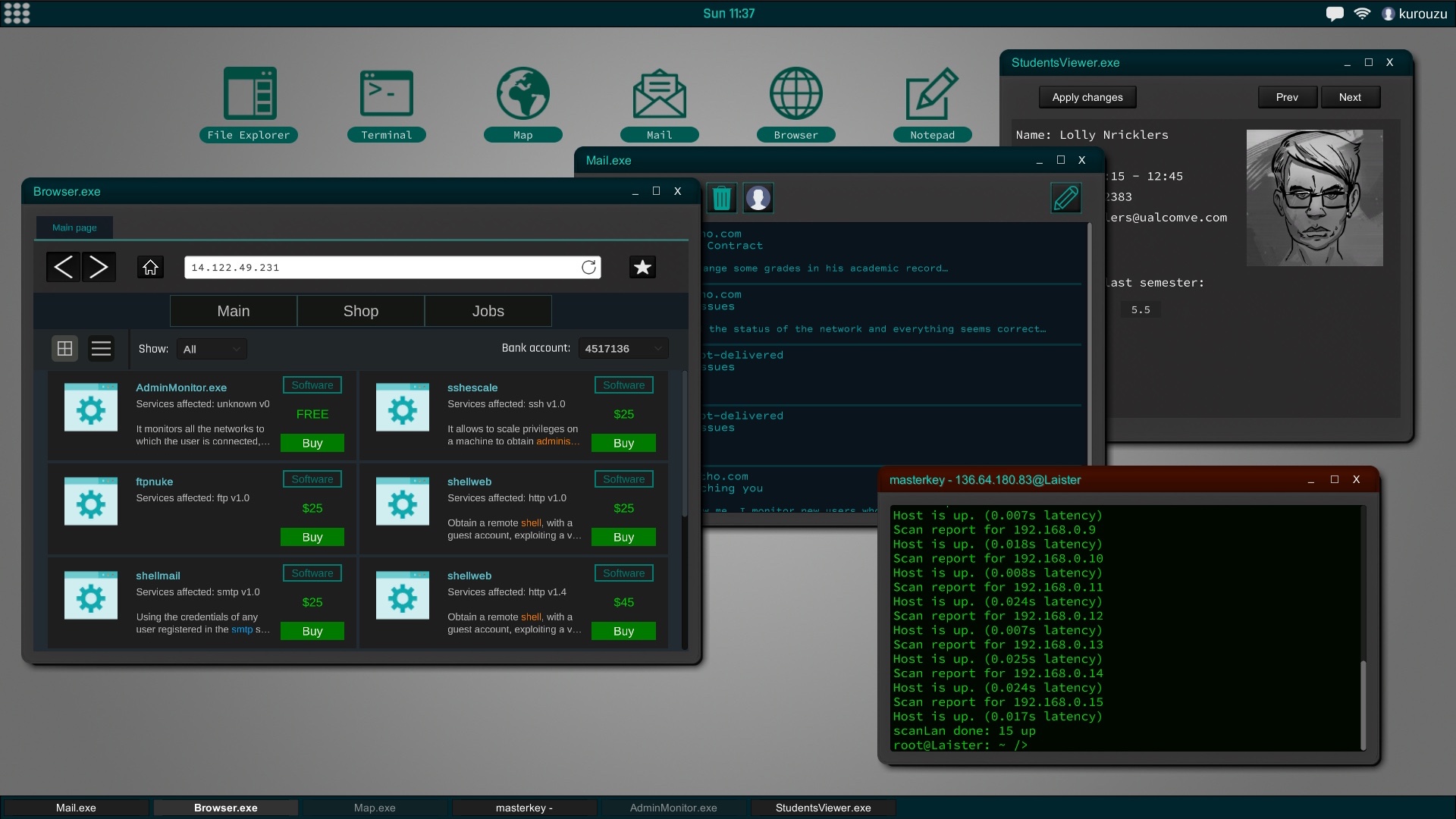
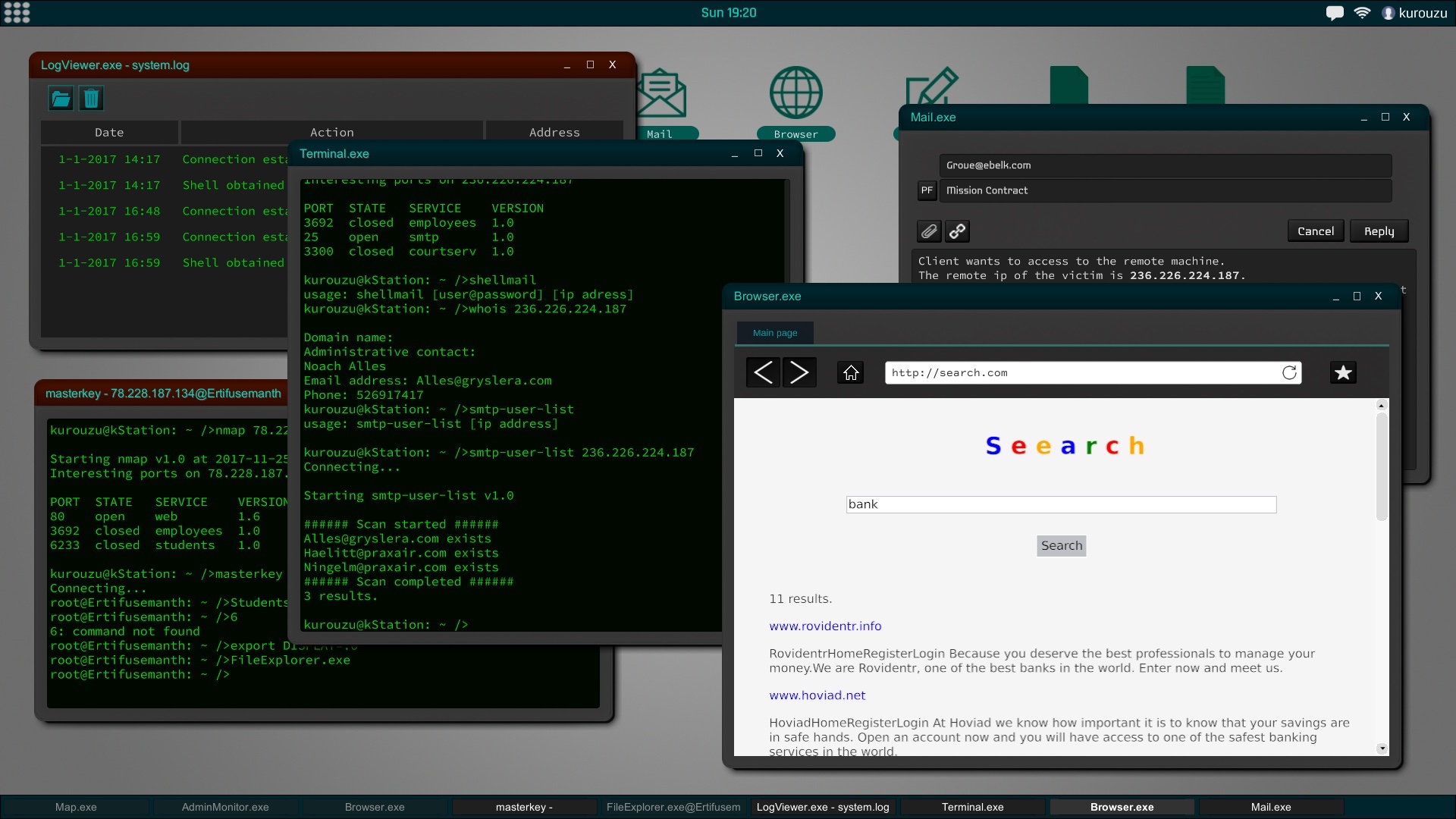
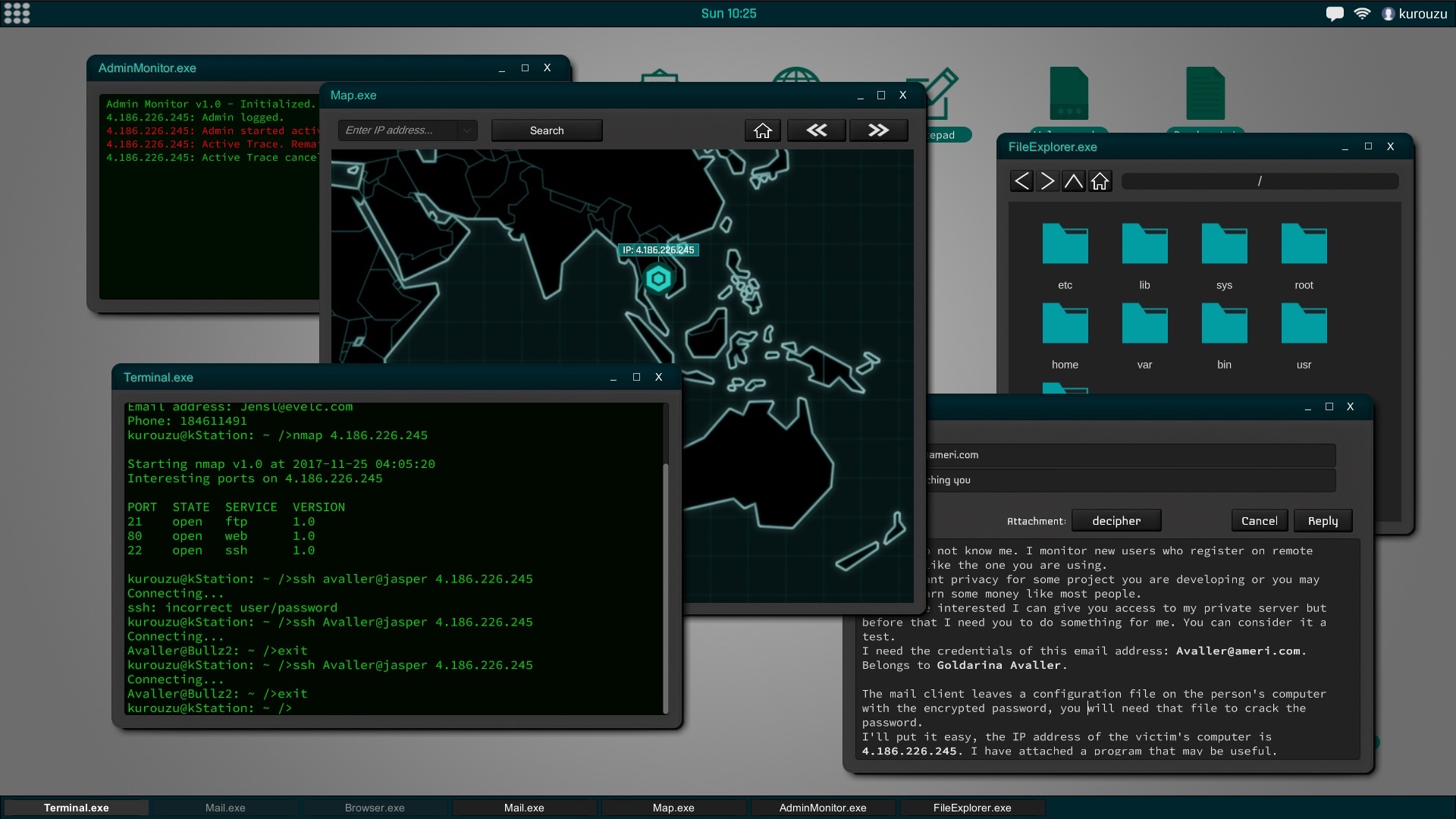
The interface of the game is similar to a current desktop operating system. The file explorer, the command terminal or text editor are some of the programs that will be available from the start of the game. As you improve your skills you will encounter new utilities may install and use.
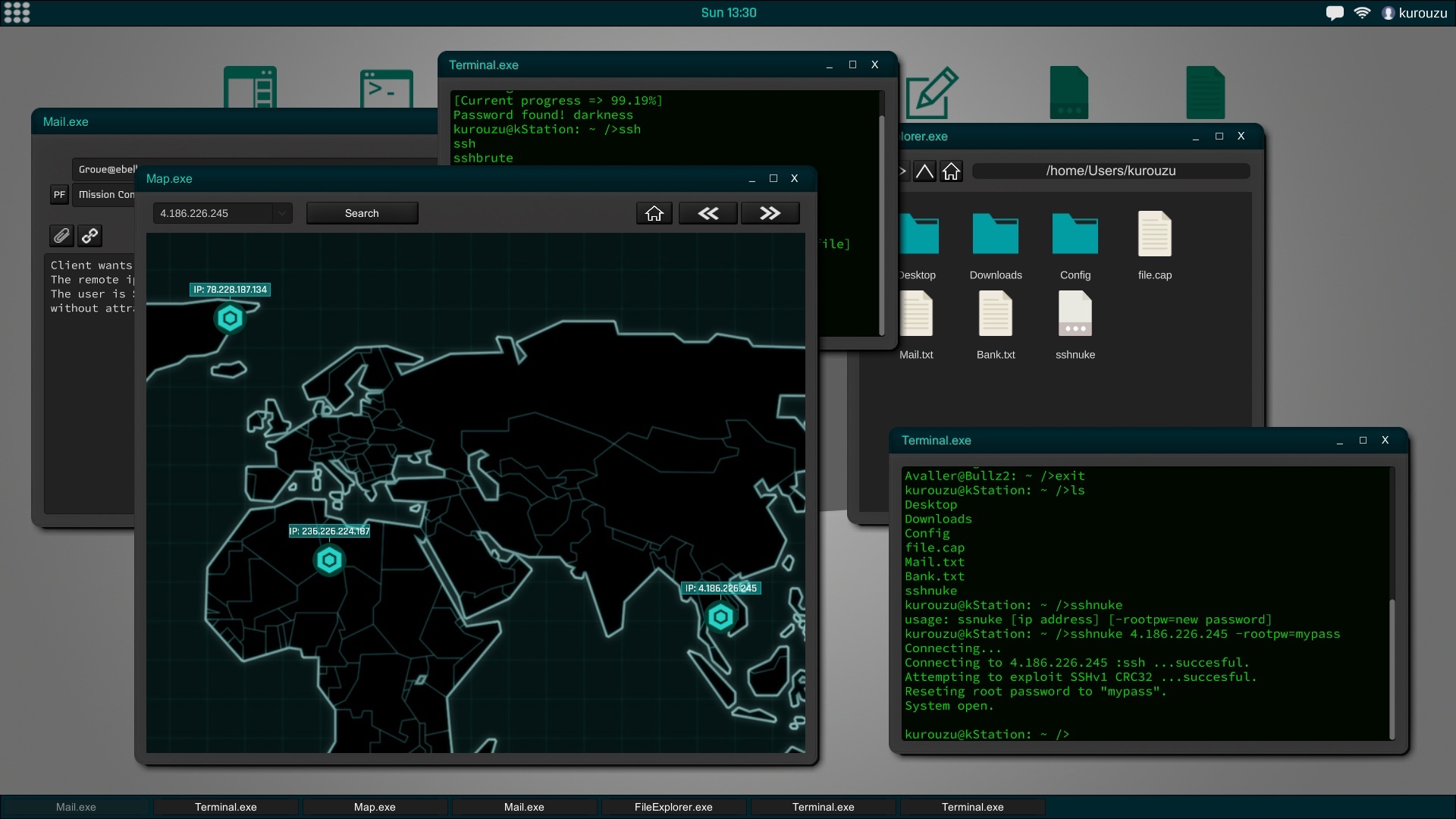
In Grey Hack, terminal has a fundamental role, it is also based on actual unix commands and will be an indispensable tool to perform successfully hacking actions.
General
Explore the network freely to discover its secrets and missions.When you increase your reputation on the network you can choose to join a group of hackers to carry out coordinated attacks or even create your own. Although if you prefer you can choose to go solo.
Keep in mind that a hacker does not have to act economically, so you decide which missions you accept and if you agree with its consequences.
Network
All computers and networks are generated procedurally to create a new experience in each game. According to the type of network the security will vary to the point of making practically impossible the penetration in certain systems according to the experience and ability that you have.Social engineering is a powerful tool and, in the most difficult cases, can be very helpful. This means that you can try to trick the user of that computer into giving you their credentials, confidential information about another person, etc.
Going to improve your work station will also be important for more and more professional jobs.
World
Each computer in the network is used by at least one user. Each user lives consistently in the world; go to work, shop online, etc. You can impact directly or indirectly in the life of these people in function of what you do.Main Features
- Simulator based on real UNIX commands.
- Operative system UI completely customizable.
- Share the same world with hundreds of players.
- Freedom to choose the type of hacker you want to be.
- Network and world generated procedurally.
- Online data persistence, allowing you to continue later in the same world and with the same computer after leaving the game.
Hi people!
I would like to share with you the latest news about the development.
As some of you know, for some time the development has been focused on the nightly build, therefore the public version will not receive updates for a while until the development of the nightly build ends and merges as usual.
Unlike previous nightly builds, this time all the features planned for this development cycle will be included before opening it for public testing.
Here are some details of what you will find in the next nightly build:
Player custom networks
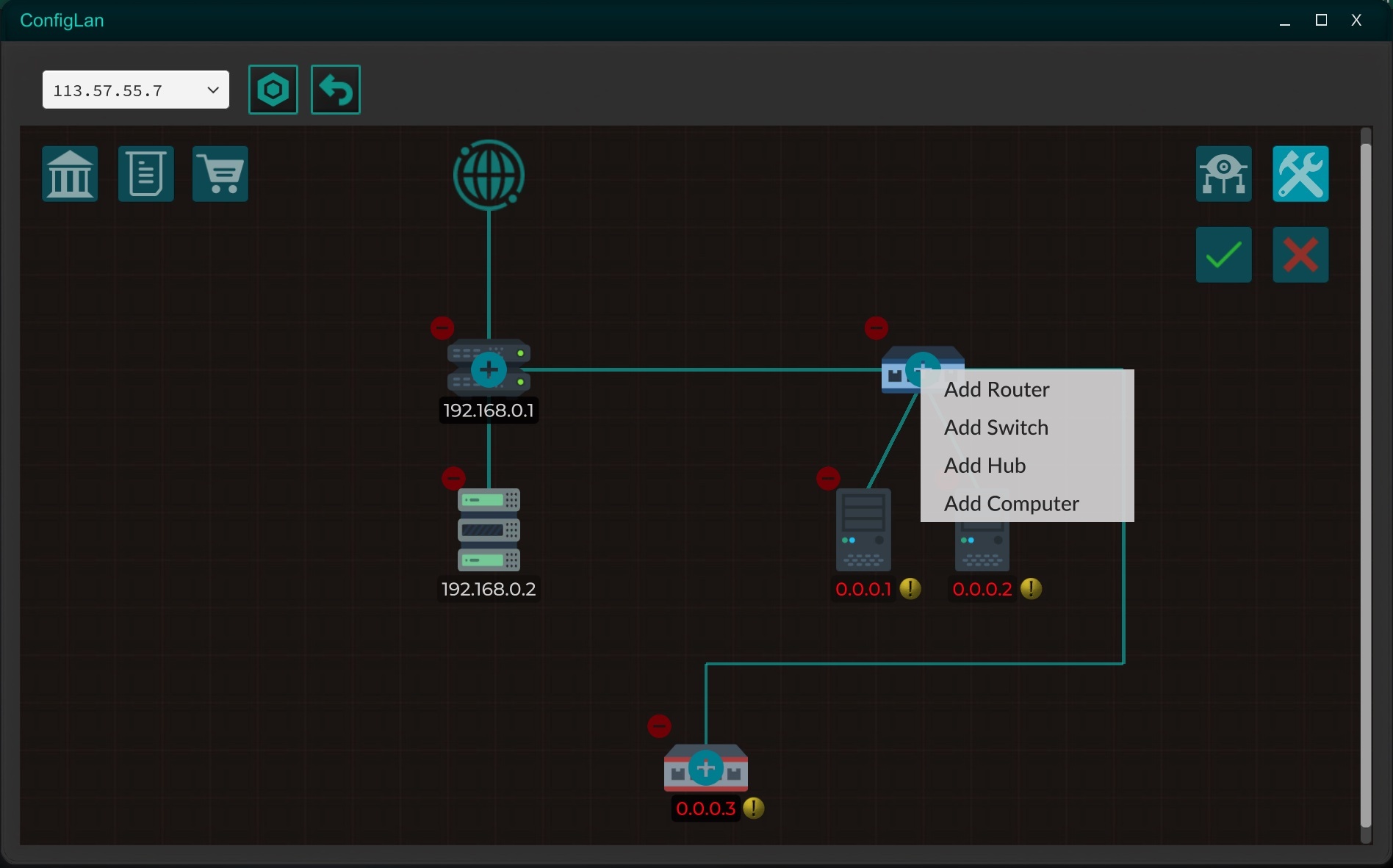
Now rented servers are expanded to rented networks!
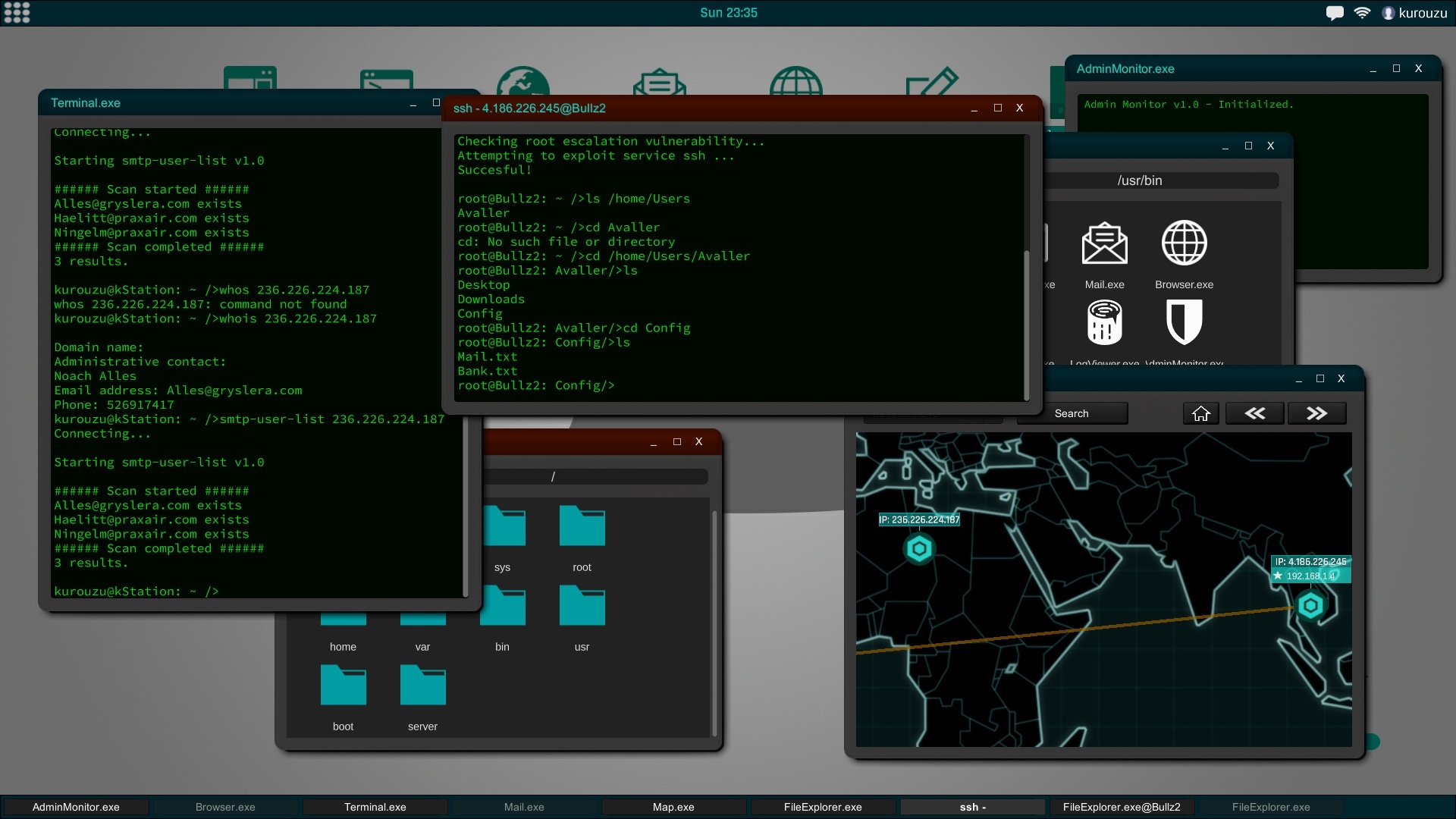
By renting a server, new devices can be added to the network, such as routers, switches, hubs or more servers to improve the security of your network, in addition to being able to add firewalls.
With the new ConfigLan tool, you will be able to remotely manage your networks, as well as reset them to their original state if for some reason you have lost the possibility of re-entering the network, either due to a configuration error or a hack.
Sniffers
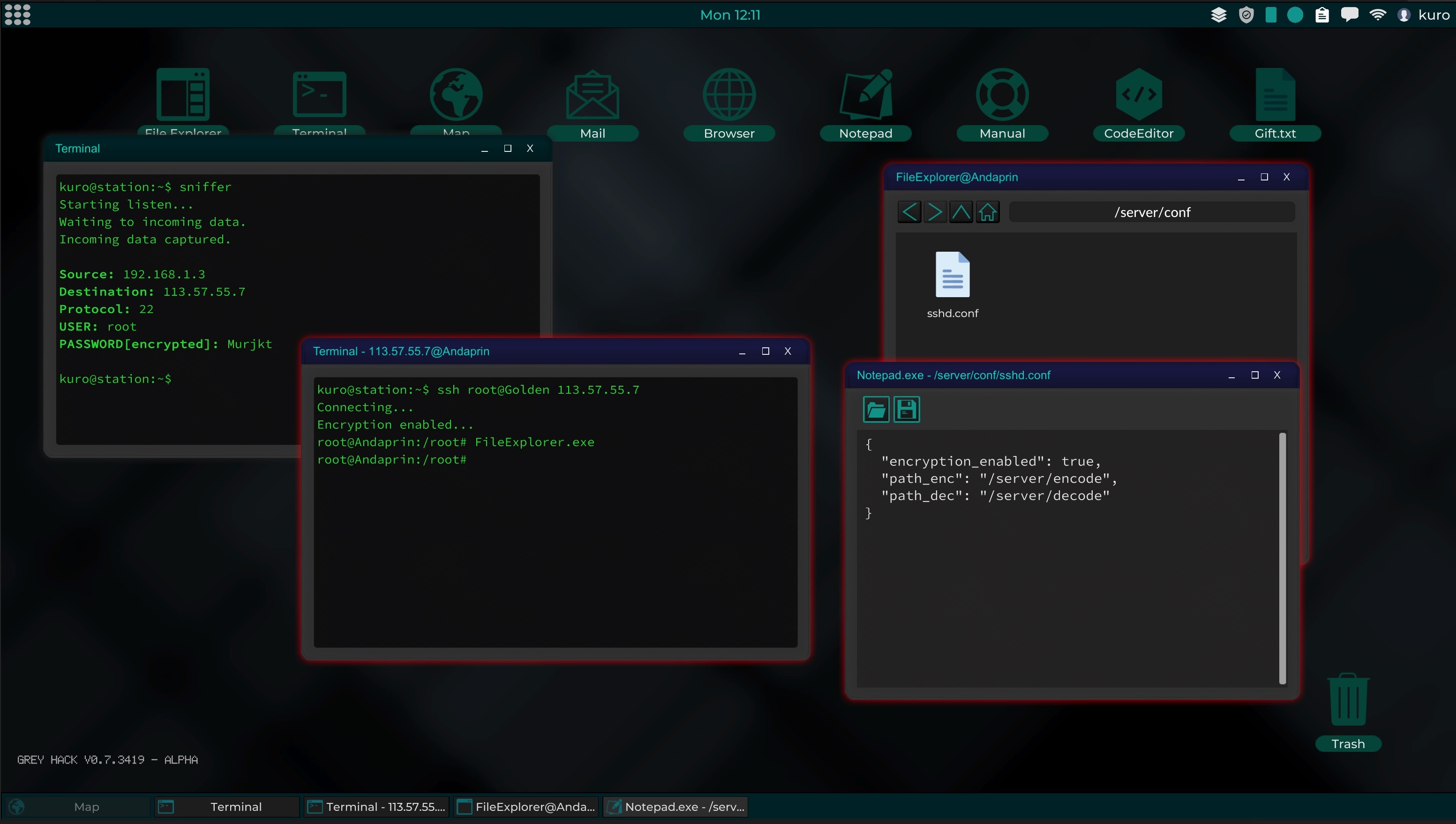
With the introduction of sniffers, players can capture the passwords of npcs and other players.
Now the ssh and ftp services allow an encrypted connection, causing sniffers to only capture encrypted passwords. Although ssh and ftp have a default encryption method, it is easily creackable, since the source code is available for study in the Manual.
Therefore players can program their own encryption system to be used with these services, so that other players can try to crack the encryption system to obtain the password.
This mechanic will consist of two scripts that will have to be installed on the server, Encode and Decode. Where sniffers can also capture the source code from Encode, but not from Decode.
As you can imagine, sniffers and encrypted connections will have more prominence in Multiplayer mode than in Single Player mode.
New devices
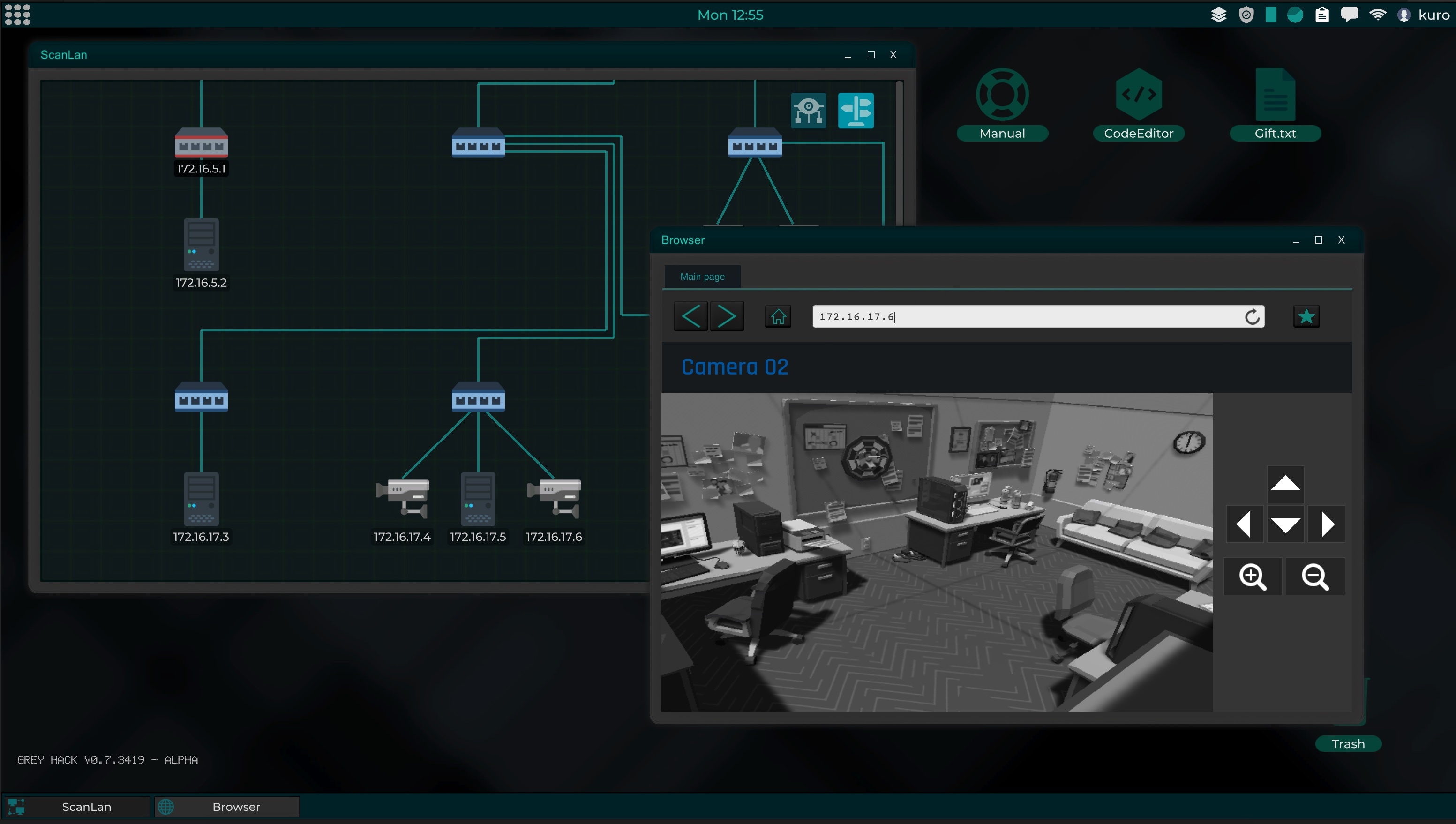
In addition to anticipated devices, such as printers or smartphones, security cameras have also been added, adding one more attack vector.
In some networks you will find security cameras installed, usually in companies, that can show the interior of these buildings. If you look closely at the environment you may find useful information.
The cameras are accessible through the browser, since they use an http server to make the connection, although they require a password to access.
New hacking techniques
New APIs will be added to the metaxploit library to allow reverse shells. That is, the victim connects to you, instead of you to the victim. This technique allows access to computers that do not have any service installed.
Reverse shells implicitly include the use of a Trojan, since to perform a reverse shell, you must first get the victim to execute your code through social engineering, and this code will install a local service that will connect to your IP as soon as possible, giving you access to a shell.
Keep in mind that you will have to have a publicly accessible service, such as ssh, for this technique to work, making you vulnerable to attacks from others.
More news soon!
Minimum Setup
- OS: Ubuntu 18.04. Ubuntu 20.04 and CentOS 7
- Processor: x64 architecture with SSE2 instruction set supportMemory: 512 MB RAM
- Memory: 512 MB RAM
- Graphics: OpenGL 3.2+. Vulkan capable
- Storage: 545 MB available space
[ 6419 ]
[ 5753 ]
[ 1960 ]
[ 2357 ]
[ 713 ]
[ 1040 ]
[ 32768 ]
[ 859 ]