It's Cyber Warfare... Turn-Based Strategy Style
Which side will you choose? The hackers (red team) or the cyber defenders (blue team)? Battle head to head in turn-based cyber warfare, where the fate of a company's computers, network, information, and even critical industrial control systems hang in the balance.But ThreatGEN: Red vs. Blue is not just a game...
Learn Real-World Cybersecurity!
Developed by actual experienced, professional (ethical) "hackers" and penetration testers, ThreatGEN: Red vs. Blue is also designed to teach you real-world cybersecurity! Learn how hackers think, operate, and attack systems by playing the part of the red team (no prior skills necessary)! Play the part of the blue team and learn about real cybersecurity controls, technology, methods, and strategies!Game Play
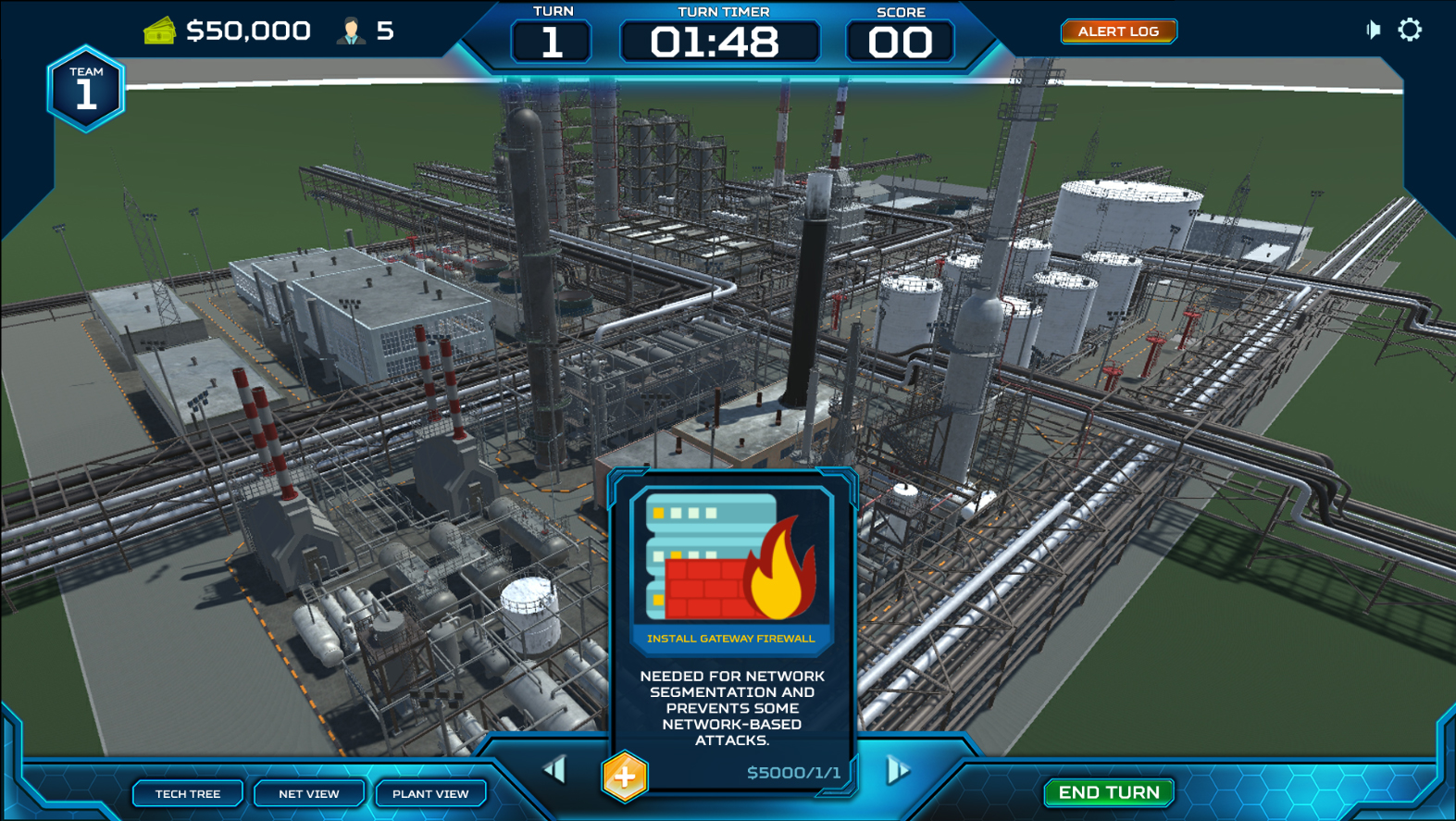
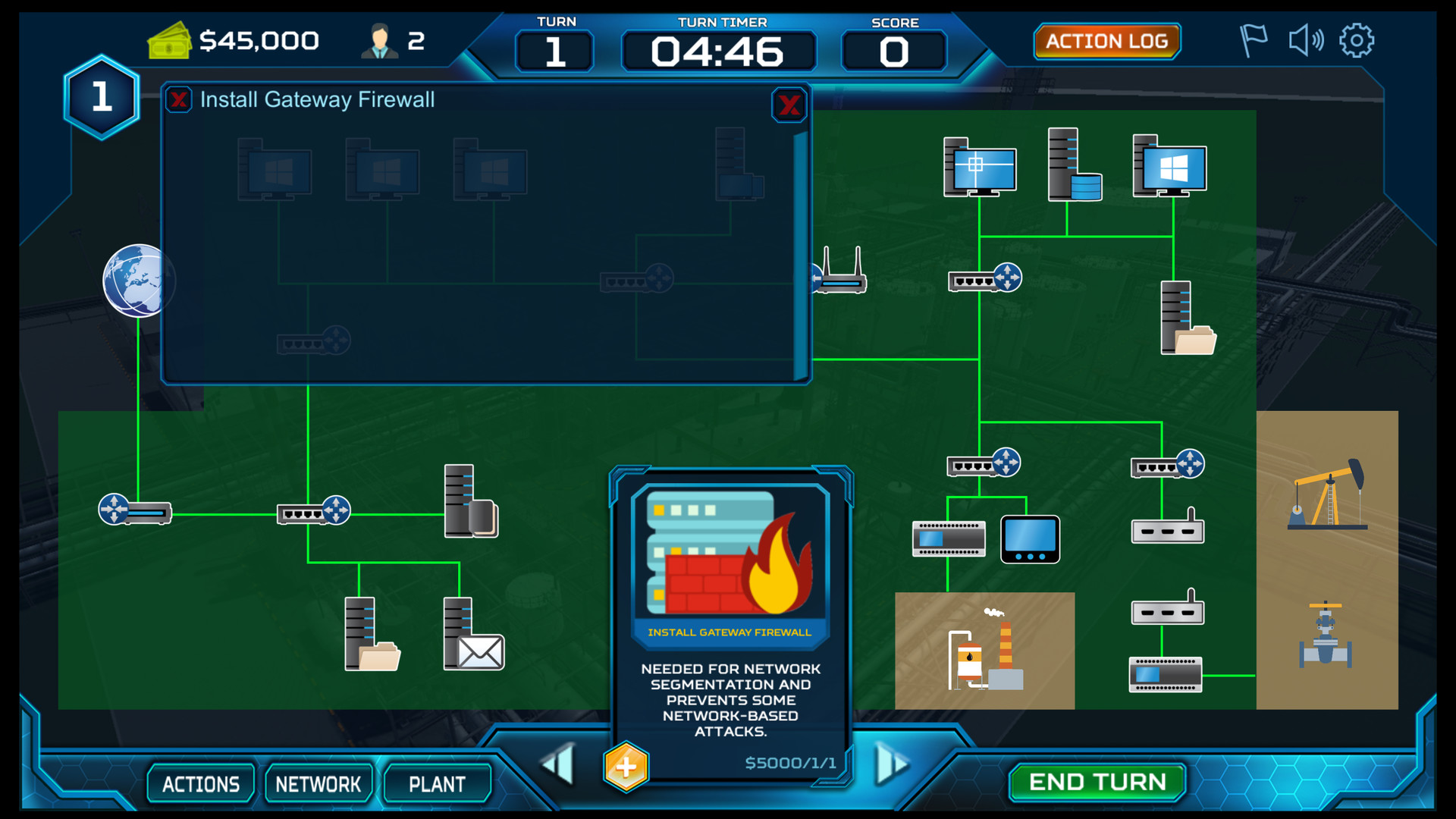
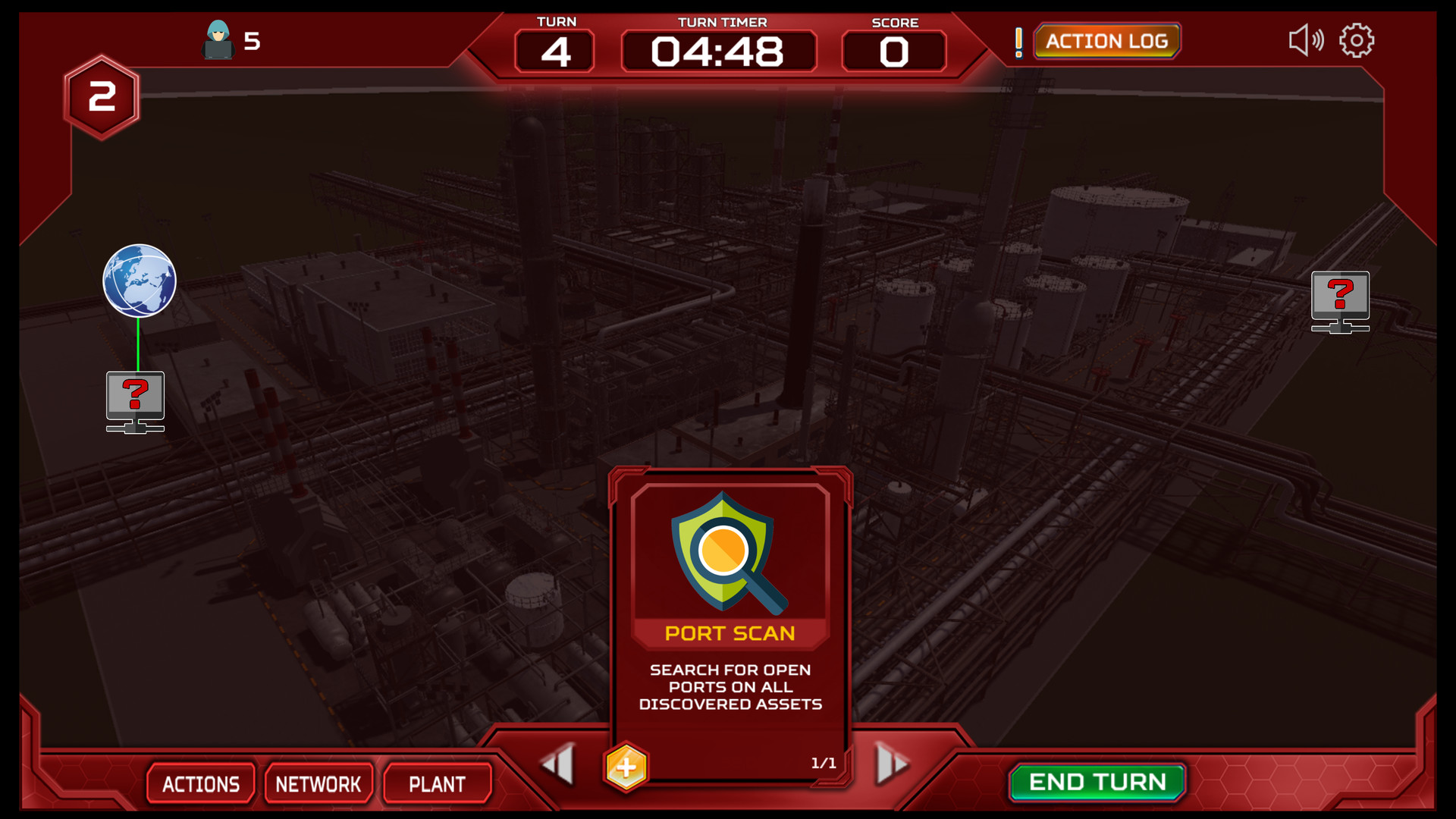
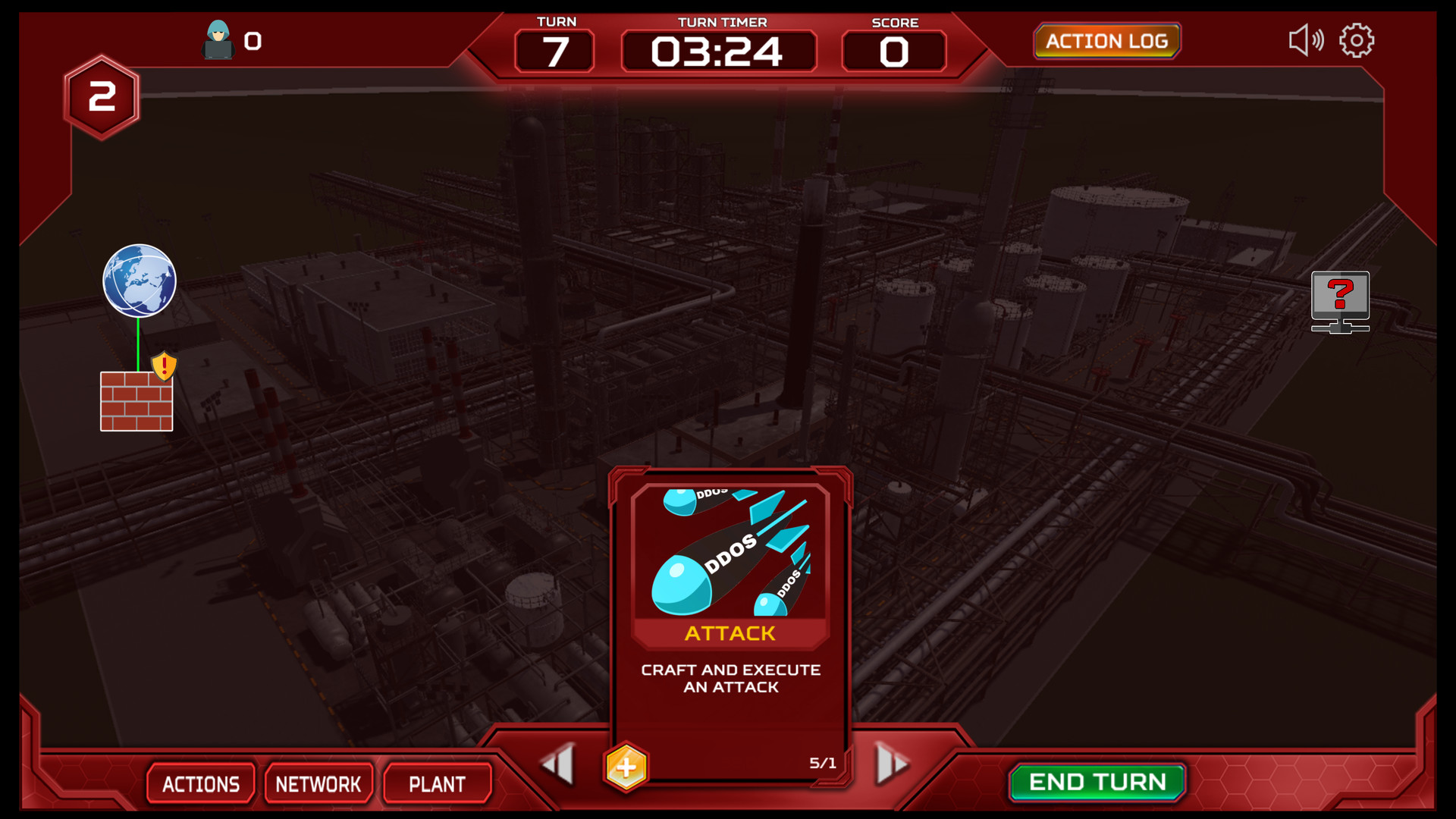
ThreatGEN: Red vs. Blue is a turn-based strategy game played much like popular global domination board games. Rather than a world map, the "game board" consists of a computer network, which players compete for control over. Instead of simulated computer terminals, players choose and commit actions using "action cards" similar to a trading card game.By the Community... For the Community
Every single member of the development team for this game actually comes from the cybersecurity (or INFOSEC) community. Most of us work, or have worked, for years as cybersecurity professionals, and we all remain active members of the community. ThreatGEN: Red vs. Blue was developed and tested as a result of the feedback from more than 300 beta testers in the cybersecurity community. Our goal is to continue to make regular updates based on continued feedback, making this truly a game by the community, for the community.Features
- Single Player vs. Computer A.I. (as red team or blue team)
- 1-on-1 internet and local hot seat multiplayer
- Cross-platform multiplayer enabled
- Touch screen optimized
- In-game real-world cybersecurity advice and hints
- Beginner tutorial
- Configurable win conditions
- "Game-pedia" with game play concepts and instructions, as well as real-world cybersecurity definitions and concepts
Version 1.10.4 released quickly after 1.10.3 to provide needed hotfixes. We were also able to add a few more feature improvements. This is expected to be the last minor update before 1.11 ships with some exciting upgrades!
Version 1.10.4 Release Notes
Fixes
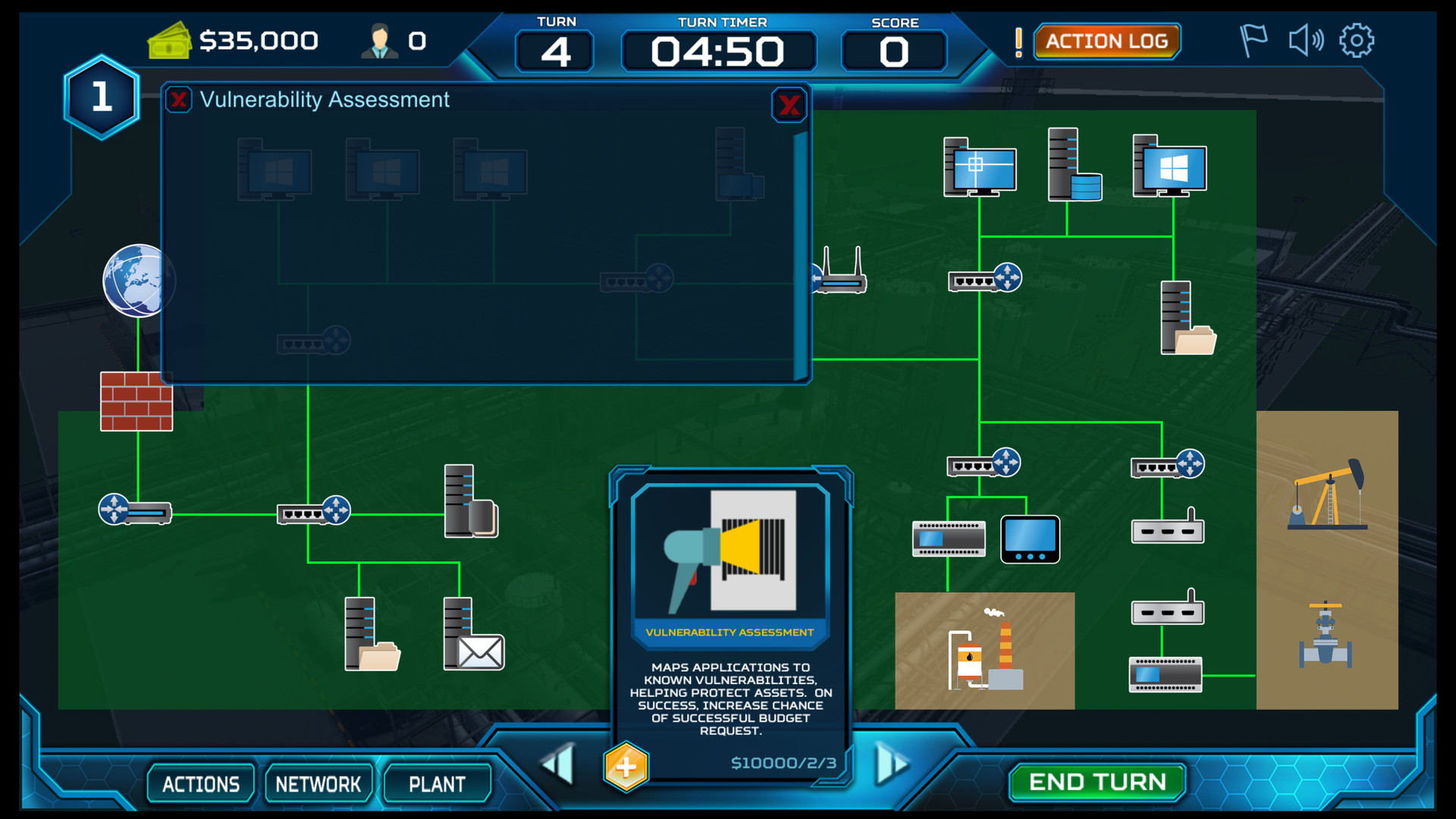
RVB1-1084 Internal Vulnerability Assessment has the requirement of implementing Asset Inventory
RVB1-1083 Internal Penetration Test has a requirement of doing at least one vulnerability assessment beforehand
RVB1-1078 Can't gather forensics on denials
RVB1-1076 Missing space between sentences in "Rogue Device Detected!" notification
RVB1-1071 Condition checkers need to be reinitialized after scenario playback
RVB1-1070 Backing up a compromised asset and restoring it gives more TI for the same compromise
RVB1-898 TTX - Loading a scenario that uses the base maps will cause the game to use that scenario every time the map is selected (incognito-only)
RVB1-602 Some close buttons on BT have red borders
Features and Upgrades
RVB1-1086 Increase chance of new vulnerabilities when patching
RVB1-1081 Added visual animation to start screen background, wiki, and notifications dialogues
RVB1-1080 Improved UI visuals (enhanced color vibrancy/saturation)
RVB1-1073 Remove Asset Inventory prereq from any action that uses it
RVB1-1072 TTX - Suppress notifications during scenario playback
RVB1-1067 Persistence research now buffs Install Ransomware and Disruptive Malware
RVB1-1066 BT Vuln assessment accelerates patch availability
RVB1-963 Asset Inventory Updates (can discover rogue device and is multi-playable)
RVB1-962 Rogue Device updates (acts as remote pivot and IDS discoverability lowered)
RVB1-936 TTX Scenario-based notification: Trigger notification when all RT control is removed
Minimum Setup
- OS: Any RPM-based or Debian-based variant
- Processor: 1.5 GHz CPU or betterMemory: 2 GB RAM
- Memory: 2 GB RAM
- Graphics: Standard onboard graphics
- Storage: 1 GB available space
[ 6425 ]
[ 3784 ]
[ 2906 ]