Midnight Protocol is a tactical narrative-driven RPG set in a near future filled with labor automation, big data, controversial AI applications, legal gray zones, and the nebulous nature of online identity. You assume the mantle of a prominent hacktivist who has been targeted for blackmail by a shadowy branch of government.
The player interacts with their virtual environment through text commands, hacking into countless challenging networks. Character development and roleplay choices made during and in between missions affect the storyline and outcome of the game.

Development on Midnight Protocol is making great progress. As we get closer to a beta version, we are excited to reveal the first gameplay details.
Real-world hacking is a methodical process and not a fast-paced caper, as it is often depicted in shows and movies. In Midnight Protocol, we wanted the best of both worlds by offering deep and strategic gameplay but also the adrenaline of breaking into a place youre not supposed to be.
Midnight Protocol was primarily inspired by RPGs and traditional board game mechanics. Lets take a look at the basics of how hacking works in this game.
The Basics
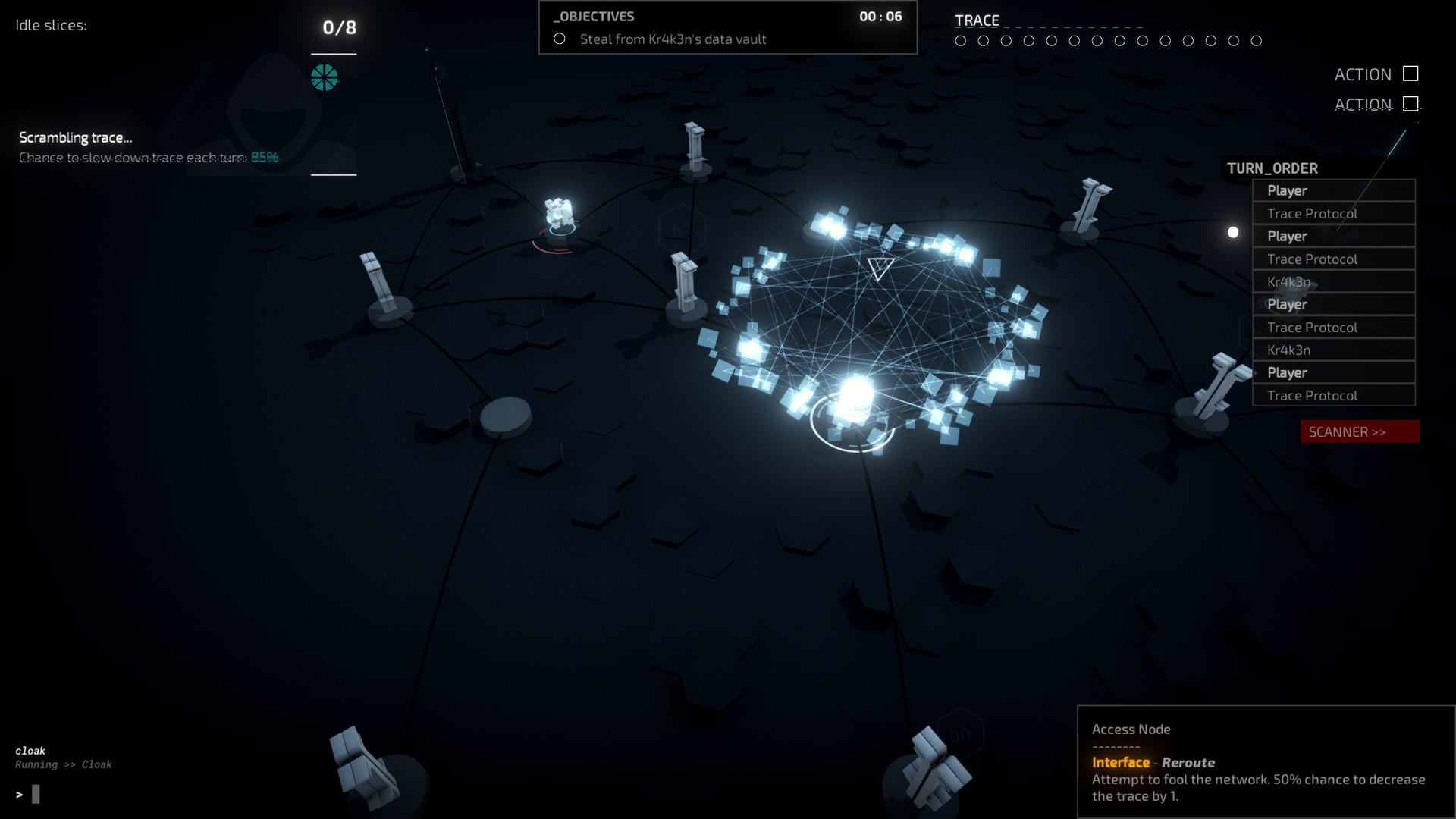
Hacking in Midnight Protocol is turn-based and takes place on a network of connected nodes. During your turn, you can spend 2 actions to do any of the following:- Move to a connected node
- Interface with your current node
- Activate a program
- Remove a running program
Your time on the network is short-lived though, as the network will attempt to trace your signal. Every turn, the trace bar will increase by one. More prudent strategies will cost more time. So the way you spend that limited time on the network is key.

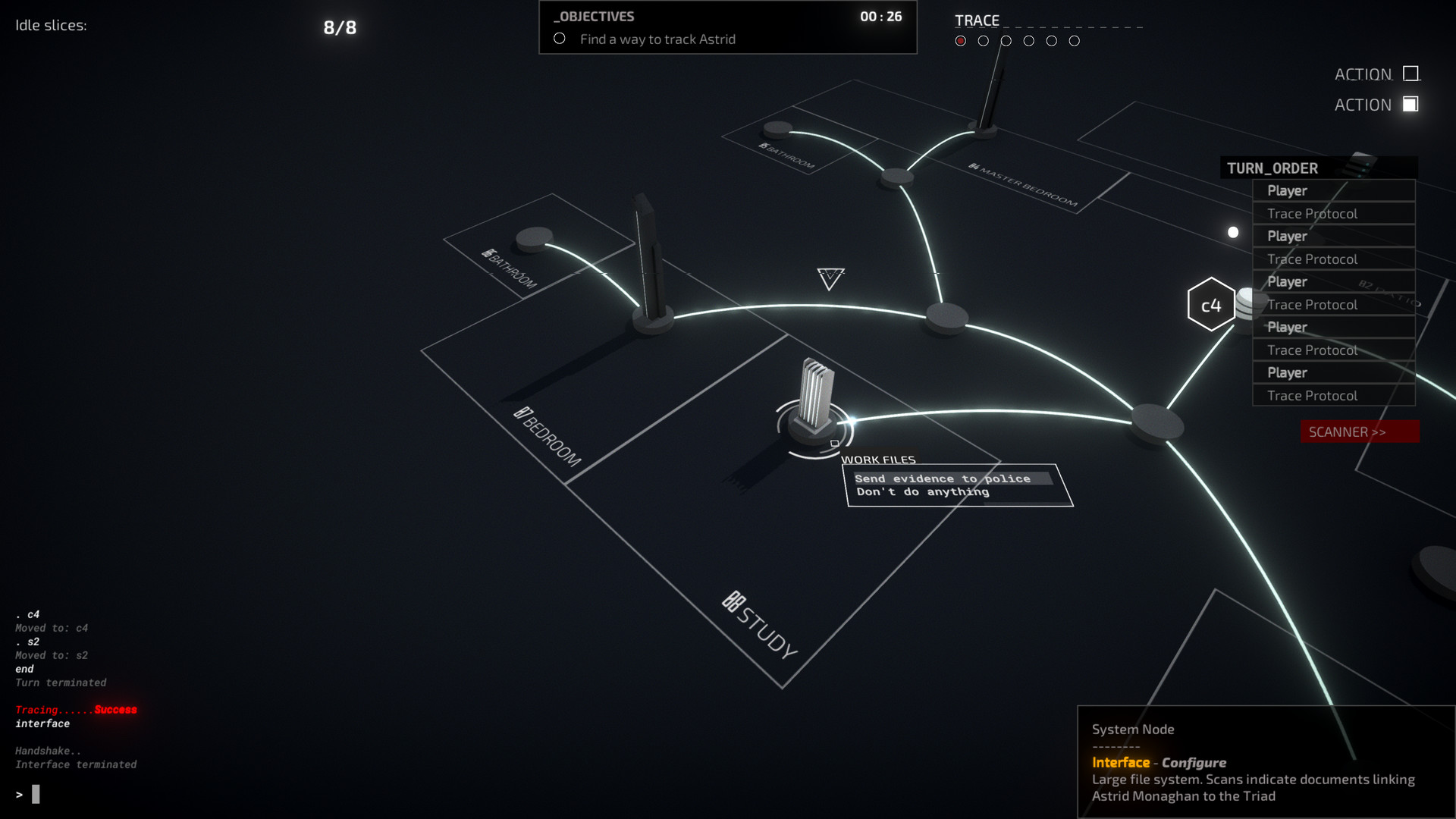
Nodes
Nodes on a network can vary from the access node where your mission starts, to financial databases, email servers, or password-protected vaults. All of these nodes offer a unique interface action. Interfacing with a bridge node, for instance, activates or deactivates certain network connections. Some node actions are more contextual, such as stopping a moving vehicle, unlocking an electronic lock or breaking into a network-connected fridge.ICE
The trace is not the only anti-intrusion measure employed by the various networks. Inspired by the classic works of William Gibson, network connections are also guarded by intrusion countermeasure electronics, or ICE for short.These network programs will generally halt your progress and apply a variety of negative effects. Their position on the network is initially hidden. As you grow more experienced with the game, you will be able to make educated guesses about which connections might contain ICE or you might use specialized programs to root them out before they can become a problem.
Once ICE is in play, you can employ dedicated programs such as Dagger of Jackhammer to tear it down. As you progress in the game, ICE becomes more dangerous and unpredictable. Some ICE will even stop hiding and go on the offensive

RESOURCES
Programs are at the heart of your strategy and determine your play style, but you can only bring a total of five programs on a mission. During the game, more programs will open up for you to buy with the credits you earn or will be awarded to you based on narrative choices you make.You wont be able to run all 5 of your programs, however. Programs you activate require processing slices to operate. You start the game with 8 of these slices and a program can have a maximum of 8 slices at its disposal. That means you can run one program at full capacity, or two at half capacity, and so on. This leads to turn-to-turn key decisions. Will you take away slices from Cloak, a program that has a chance to stop the network trace every turn, to empower Dagger, the program that is tearing down a Binary Wall? Will you sacrifice Leech, a program that is draining credits from a financial server in favor of cracking that vault node just a little bit faster?
Additionally, some programs offer only an immediate benefit but cannot be removed for a set amount of turns. Sniffer, for example, will immediately tell you if a connection is guarded by ICE, but will continue to occupy 2 slices for another 2 turns.
The slices system is also a potential target for the many different types of ICE you will encounter. Some ICE will install malware that will eat up your slices until properly removed. Scorpion, for instance, inflicts you with a program called Poison that will use your own slices to increase the trace every turn but can be manually removed by spending an action.

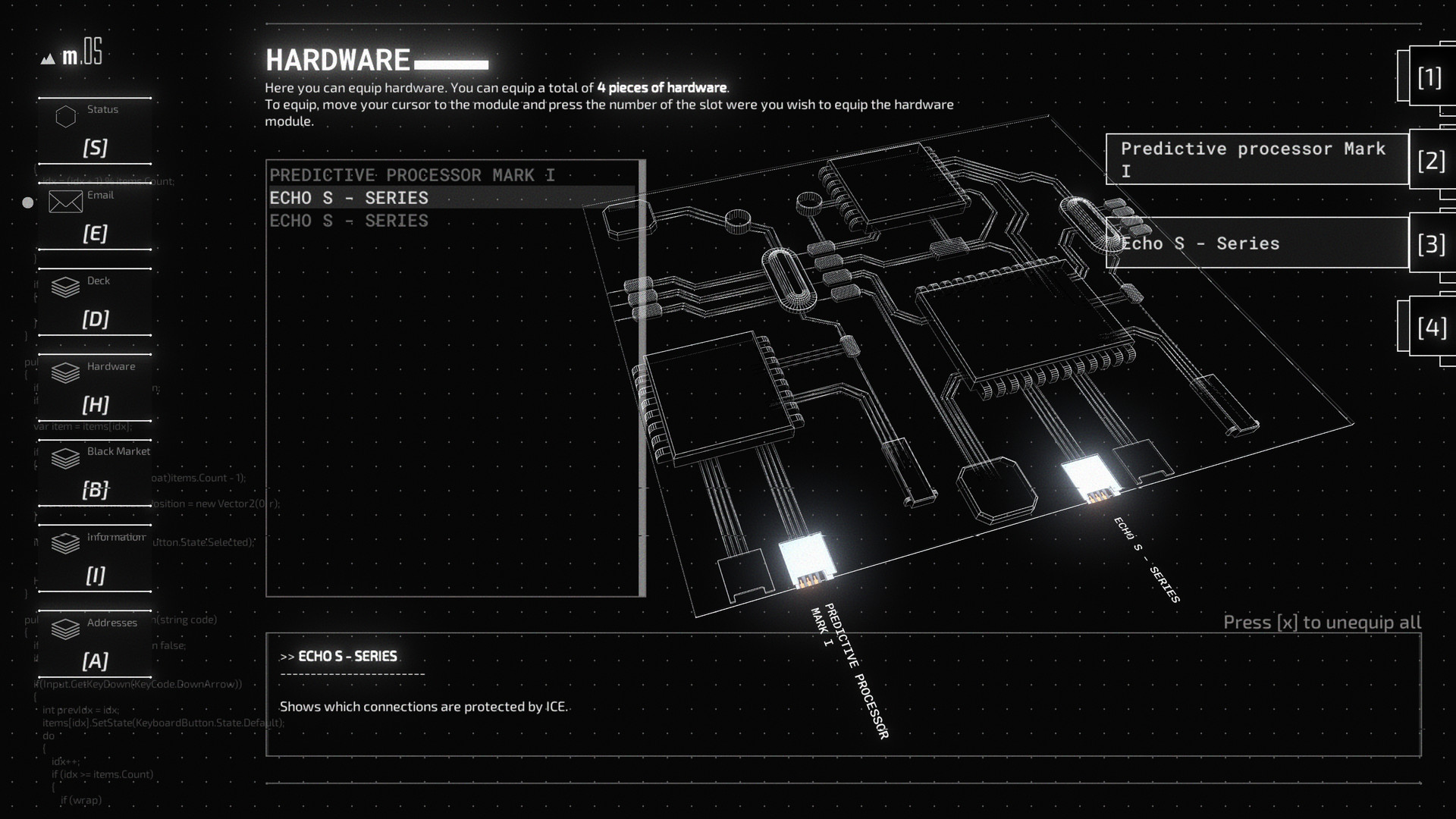
Advanced Tools
There are many more things to consider while playing. Hardware will give you passive upgrades. Challenges require you to mix up your strategy in exchange for cash. Finally, there are also system operators who have an active turn on the network and who employ deadly, dedicated programs to root out any hacker on the network.These mechanics turn every level into a puzzle where you try to figure out the best strategy for surviving on the network and force you to take risks in a situation where you dont have complete information.
Will you play it safe? Or will you risk running into ICE?
[ 6372 ]
[ 5860 ]
[ 1991 ]
[ 1943 ]
[ 986 ]